The Smart Move to Phishing-Resistant Multi-Factor Authentication
By Dr. Julius Smith and Tim Coogan | 11/26/2025
BY DR. JULIUS SMITH
Vice President & Chief Information Officer
Dallas Area Rapid Transit
Chair, APTA Security Standards, Transit Cybersecurity Working Group
AND TIM COOGAN
Director and CISO, Cybersecurity
Denver Regional Transportation District
Vice Chair, APTA Security Standards, Transit Cybersecurity Working Group

Public transit agencies are becoming increasingly digital. Fare systems, CAD/AVL platforms, real-time vehicle data, workforce management systems, on-board systems, operational technology, and cloud-hosted ERP platforms have dramatically expanded the attack surface. At the same time, cyber attackers are using AI to craft compelling phishing emails, SMS messages, and spoofed login portals designed to steal usernames and passwords.
Transit leaders may not be able to control how threat actors operate, but they can control the level of authentication required before anyone, the staff or attacker, accesses the network. That is where phishing-resistant multi-factor authentication (MFA) becomes essential.
Tim Coogan in Denver routinely expresses that “cybersecurity phishing-resistant MFA is not simply stronger MFA.” It is a fundamentally different approach that removes the attacker’s ability to steal or replay authentication. Traditional MFA methods, SMS codes, email links, or one-time passwords, were once considered secure. Today, attackers bypass them routinely using AI tools, real-time man-in-the-middle kits, and session hijacking malware. The result is that many agencies still believe they are protected, yet they rely on MFA methods that attackers have already learned to defeat.
As AI increases the frequency and sophistication of phishing attacks, leaders must adopt authentication methods that attackers cannot socially engineer, intercept, or bypass. The investment is significantly smaller than the cost of a significant breach, system outage, or operational disruption.
Below are the benefits, practical considerations for transit, and real-world lessons for transit agencies evaluating or implementing phishing-resistant MFA.
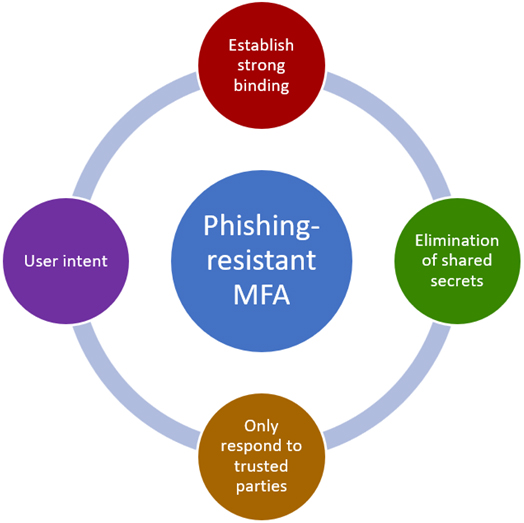
What is Phishing-Resistant MFA?
The term is defined by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and NIST. Phishing-resistant MFA uses cryptographic authentication methods that ensure that:
- Authentication cannot be completed on a fake website.
- Credentials cannot be intercepted or reused.
- The login credential is bound to the real website or system only.
The two primary standards today are:
- FIDO2/WebAuthn security keys (hardware tokens or built-in platform authenticators).
- PIV or CAC-style smart cards or equivalent certificate-based authentication.
Both work by using private cryptographic keys that never leave the device. A malicious actor cannot phish, intercept, or replay them. Importantly, this is true even with AI-powered tools.
Why This Matters for Transit Agencies
1. Operators, dispatchers, and maintenance teams are prime phishing targets.
Any user with access to operating systems is valuable to attackers. One transit agency experienced repeated phishing waves targeting maintenance staff because attackers learned that maintenance accounts had access to both inventory systems and remote diagnostic tools. Traditional spam filters failed to catch any of the fraudulent emails because they were AI-generated, highly personalized, and referenced real bus models. Phishing-resistant MFA would have stopped the attacker even if the employee clicked the link.
2. Cloud adoption is increasing the attack surface.
Fare collection systems, ERP applications, workforce scheduling, and procurement systems are often cloud-based. As agencies migrate legacy systems, attackers follow the data. The majority of modern breaches begin at the login page—not through firewalls. Phishing-resistant MFA closes the most common door.
3. Ransomware now uses session hijacking.
A growing trend is the use of man-in-the-middle frameworks by ransomware operators to intercept MFA codes in real-time. A transit scheduling coordinator may think they successfully authenticated, while the attacker uses the intercepted session token to access fleet scheduling, executive email accounts, or payment systems. Security keys make session hijacking practically impossible.
4. It supports Zero Trust, which the federal government encourages.
Agencies moving toward Zero Trust architectures quickly learn that password-based systems are incompatible with accurate identity verification. Phishing-resistant MFA is often the first significant milestone in a Zero Trust roadmap.
Practical Examples for Transit Operations

Stopping fake “dispatch instructions.”
A dispatcher receives an email that appears to be from a supervisor, asking them to update route assignments for a special event. The link leads to a spoofed login page. With SMS-based MFA, the attacker could intercept the one-time code and use it to complete the login. However, with a FIDO2 key, the key will not authenticate on the fake website. The attack ends instantly.
Protecting Executive Approvals and Procurement Workflows.
A finance director receives a fraudulent invoice and is prompted to log in to review it. Traditional MFA could be bypassed with a relay attack. With certificate-based authentication bound to the agency’s true ERP domain, the attacker cannot complete the login, even if they replicate the ERP interface perfectly.
Safeguarding Remote Workforce Management Systems.
Drivers bidding for shifts do so online, and attackers are aware that these systems contain personal data. By using phishing-resistant MFA, operators authenticate with hardware keys or mobile device-based platform authenticators that cannot be transferred, cloned, or reused.
How to Begin Implementation
1. Start with high-risk systems.
Prioritize:
- Executive accounts
- IT and OT administrators
- Dispatch and operational control systems
- ERP and financial systems
- Fare collection and customer accounts
2. Select standards-based technology.
NIST SP 800-63 and CISA guidelines strongly recommend FIDO2/WebAuthn. Transit agencies should avoid proprietary systems that lock them into a single vendor.
3. Provide staff training with real examples.
Hands-on practice reduces resistance. Many agencies conduct “key fairs” where staff set up their security keys with on-site support.
4. Ensure backup methods.
Use secondary hardware keys or a secure recovery process to avoid lockouts.
5. Communicate clearly that this protects people, not just systems.
Employees are more receptive when they understand MFA stops attackers from impersonating them, not just blocking access.
The agencies that move early will be the ones best protected as cyber threats continue to evolve.

References
CISA. Implementing Phishing-Resistant MFA.
NIST SP 800-63-3: Digital Identity Guidelines.
FIDO Alliance. FIDO2 & WebAuthn Specifications.
Microsoft Security Blog. Evolving Credential Threats and MFA Bypass Trends.
CISA & TSA. Surface Transportation Cybersecurity Toolkit.